Understanding Legal and Illegal Hacking
Introduction
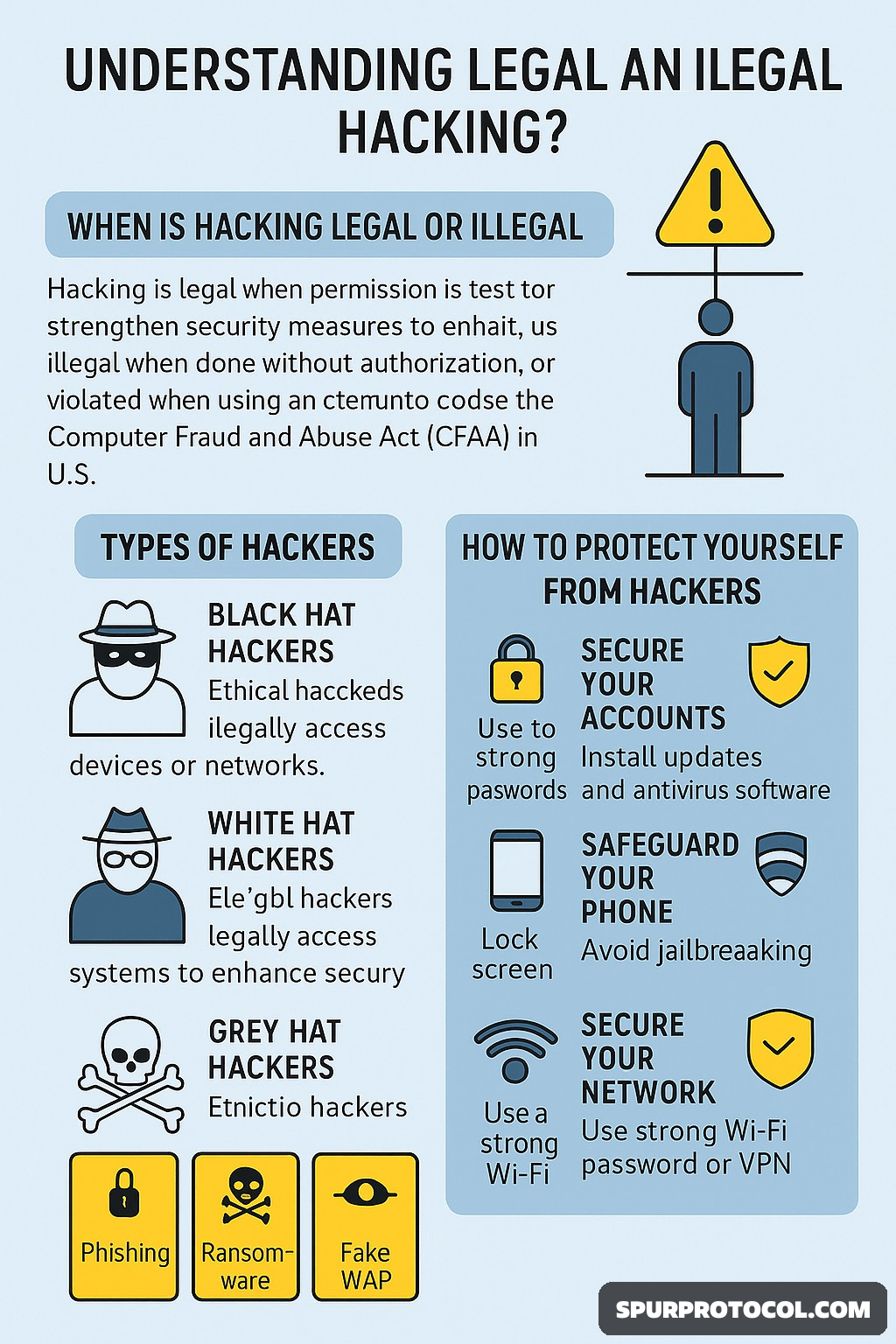
In today's digital world, hacking can be a force for good—or a weapon of destruction. The same skills used to protect networks can also be used to steal data, hold systems hostage, or damage reputations. The difference lies in intent and authorization. This article breaks down when hacking is legal or illegal, the types of hackers out there, and how you can protect yourself from cybercriminals.
When Is Hacking Legal or Illegal?
Hacking is legal when done with permission to test or strengthen security (e.g., penetration testing). It becomes illegal when a hacker accesses systems or data without authorization—violating laws like the Computer Fraud and Abuse Act (CFAA) in the U.S.
Types of Hackers
1. Black Hat Hackers
These are cybercriminals who illegally access devices or networks to steal, destroy, or exploit data. They may use tools like ransomware, viruses, Trojans, and worms. Some work solo, while others are part of organized crime rings. They're behind over 2,000 cyber breaches daily.
2. White Hat Hackers
Also known as ethical hackers, they legally test systems to identify vulnerabilities and protect against cyberattacks. Many use the same tools and techniques as black hats but with permission and good intent—often working for businesses, governments, or cybersecurity firms.
3. Grey Hat Hackers
Operating in a legal gray zone, these hackers access systems without permission but usually without harmful intent. Some report flaws, while others expose sensitive data, as seen with whistleblower platforms like WikiLeaks. Some grey hats are simply honing their skills or working as bug bounty hunters.
Legal Hacking: Types of Penetration Testing
1. White Box Testing – Full access and information provided; simulates insider threats.
2. Black Box Testing – No access or information; mimics a real-world cyberattack.
3. Gray Box Testing – Limited access; tests both internal and external vulnerabilities.
Illegal Hacking Techniques
Black hat hackers use a variety of tactics, including:
1. Phishing – Fake emails or messages trick users into clicking harmful links.
2. Ransomware – Locks users out of their systems until a ransom is paid.
3. Keyloggers – Secretly record keystrokes to steal passwords and other data.
4. Fake WAPs – Imitation WiFi networks that steal data from connected devices.
5. Bait and Switch – Malicious ads or downloads disguised as legitimate content.
Is Hacking a Crime?
Yes—accessing a computer or network without permission is a criminal offense. Violations include:
1. Deleting or damaging data
2. Sending spam
3. Buying/selling stolen credentials
4. Unauthorized access to devices or networks
5. Defrauding individuals using ICT skills
6. Accessing national security information
7. Blackmail and extortion
How to Protect Yourself from Hackers
1. Secure Your Accounts
I Use a password manager
II. Enable two-factor authentication
III. Avoid sharing passwords
IV. Use fake answers for security questions
V. Always log out on public devices
VI. Ensure websites show a secure padlock (HTTPS)s
2. Protect Your Mobile Devices
I. Regularly update phone locks
II. Enable automatic app updates
III. Use proper chargers in public
IV. Don’t jailbreak or root devices
3. Safeguard Your PC
I. Encrypt hard drives
II. Install OS and software updates
III. Backup data frequently
IV. Use antivirus and anti-malware tools
V. Avoid suspicious links or downloads
VI. Enable firewall and firmware passwords
VII. Disable remote access unless needed
4. Secure Your Network
I. Use strong WiFi passwords
II. Connect to public WiFi only via VPN
III. Avoid excessive personal info online
IV. Download files only from trusted sites
V. Avoid torrenting or file-sharing platforms
VI. Shop only on verified eCommerce sites
Conclusion
Now that you understand the difference between white hat (ethical) and black hat (criminal) hackers, as well as the legal and illegal aspects of hacking, it's your responsibility to stay informed and proactive. By following the cybersecurity tips shared above, you can protect your data, devices, and networks from falling into the wrong hands.