What Is A Dusting Attack?
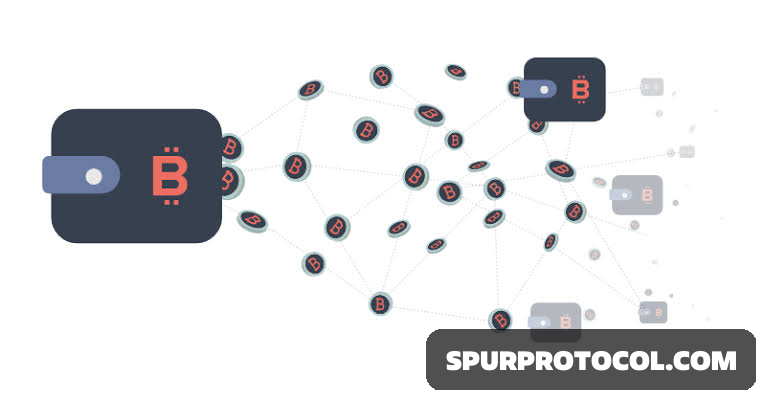
When an attacker transfers little amounts of money to Bitcoin or crypto wallet, this is known as a dusting attack.
Go Back
🕒 4:23 PM
📅 May 22, 2025
✍️ By Ecojames
What is a Dusting Attack
A crypto dusting attack involves sending small quantities of cryptocurrency, known as dust, to numerous wallet addresses to track and de-anonymize them.
Dusting Attack Detection Methods
1. Transaction Monitoring
- Cryptocurrency wallet providers and users can implement systems to monitor incoming transactions for unusually small amounts of cryptocurrency.
- Transactions involving amounts that are significantly below the typical transaction size can be flagged for further analysis.
2. Address Clustering Analysis
- Blockchain analysis tools can be used to identify addresses that are linked together through dust transactions.
- By tracking the flow of these small amounts across different addresses, it is possible to detect patterns that suggest an attempt to de-anonymize users.
- Clustering algorithms can help identify suspicious activity and highlight potential dusting attacks.
3. Behavioral Analysis
- Examining the behavior of transactions over time can help in detecting dusting attacks. For example, if an address suddenly starts receiving multiple small transactions from unknown sources, it could be a sign of a dusting attack.
4. Alert Systems
- Implementing alert systems within cryptocurrency wallets can help users quickly respond to potential dusting attacks.
- These systems can notify users when they receive transactions that fall below a certain threshold, allowing them to take preventive measures such as moving their funds to a new address or using privacy-enhancing techniques to obscure their transaction history.
How to Protect Yourself from Dusting Attack
1. Ignore unsolicited small transactions ("dust") sent to your wallet.
2. Do not interact with links or messages included in memo tags or unsolicited transactions.
3. Use a new receiving address for each transaction, especially for cryptocurrencies that support changing addresses.
4. Never share your 24-word recovery phrase with anyone. Ledger will never ask for it.
5. Stay vigilant when receiving unexpected transactions or messages.
6. Regularly monitor your accounts for any unauthorized activity.

