What Is Key Derivation Function (KDF)?
A Key Derivation Function (KDF) is a cryptographic algorithm used to securely derive one or more secret keys from a master secret, such as a user's password or a master seed phrase. KDFs are a crucial security mechanism designed to slow down brute-force attacks by intentionally adding time and computational cost to the key generation process.
Go Back
🕒 7:32 AM
📅 Oct 27, 2025
✍️ By Nathanael707
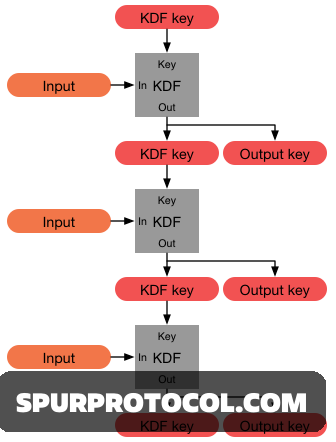
Defining the KDF's Security RoleA Key Derivation Function (KDF) takes a low-entropy input (like a memorable password) and uses a resource-intensive, iterative process to transform it into a high-entropy, cryptographically secure output (the key). The process is intentionally made slow and complex, requiring a significant amount of computational power, time, and memory. This slowness is a feature, not a bug, designed to thwart attackers who attempt to test millions of possible passwords per second.
Input: Low-entropy secret (e.g., password, seed phrase).
Output: High-entropy, secure cryptographic key.
Security Feature: Costliness (time and memory) designed to slow down brute-force attacks.
Standard: Commonly used KDFs include PBKDF2, Scrypt, and Argon2.
The Role of Iteration and Salt
Two main components ensure the security and uniqueness of the derived key.
Salt: A unique, random value added to the password before hashing. The salt ensures that the same password generates a different output key for every user, defeating the use of pre-computed hash tables (rainbow tables).
Iteration Count: The number of times the hashing function is applied. A high iteration count significantly increases the time needed for a brute-force attack, making it economically unviable.
Utility in Wallet Security
KDFs are essential for the security of mnemonic seed phrases and local wallet files.
Seed Phrase Conversion: KDFs (like PBKDF2 in BIP-39) convert the 12-24 words into the master seed used to generate all private keys.
Local Wallet Encryption: Used to derive a strong key from a user's local password, which is then used to encrypt the private keys stored on a device.
